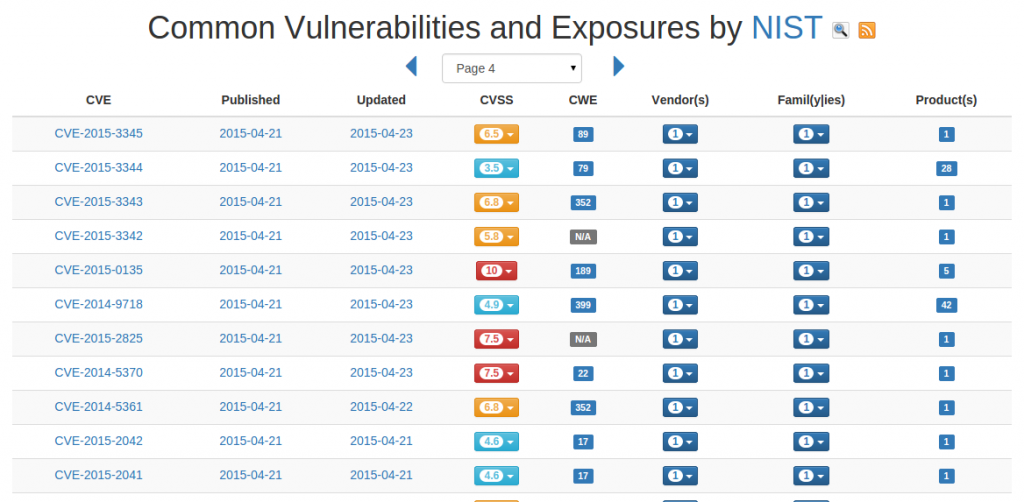
As you can see, Pentest.IT has a new look and feel and some new feature available. Dozens of minor bugs have been fixed. To avoid too long select lists in search forms, the <selecte> element has been replaced by the newest <datalist> element.
Many thanks to Bootstrap Framework developers, that make web design something possibile also to me!
This is first time I write FAQ for this service. Considering I’m the main (and only) developer there’s no question I need to do, but maybe a lots of questions I should reply to. So, feel free to ask for more details in the comments below.
What is the Pentest.IT’s mission?
Pentest.IT has not specific mission. You have to consider it just as an aggregation center for public CVEs. The purpose (not the mission) is to help people and organizations in the vulnerability management process.
What does it mean CVE?
CVE is the acronym for “Common Vulnerabilities and Exposures”. The MITRE () defines CVEs has “…a dictionary of publicly known information security vulnerabilities and exposures“.
What is a Vulnerability and an Exposure?
A “vulnerability” is a mistake in software that can be directly used by a hacker to gain access to a system or network.
An “exposure” is a system configuration issue or a mistake in software that allows access to information or capabilities that can be used by a hacker as a stepping-stone into a system or network.
The different between vulnerability and explosure is that the first one is usable to compromise a system. An exposure, even if is not usable itself to hack a system, is usually an important component of a successful attack.
What does it mean CWE?
CWE is the acronym for “Common Weakness Enumeration“. CWE provides a dictionary of commons software weaknesses. When a CWE is associated to a CVE entry the vulnerability is more detailed in its weak point. By this way it should be easiest apply security solution such as logical or physical security.
Note that a CWE entry describe just a weak point. It doesn’t specify how an attacker could gain advantage by the vulnerability. The attack methodologies are listed by the CAPEC dictionary.
What does it mean CAPEC?
CAPEC is the acronym for “Common Attack Pattern Enumeration and Classification“. CAPEC provides a dictionary of commons attack methodologies with the scope of understanding how a real attack can be performed and a better defence strategy could be applied.
CAPEC are usually mapped to one or more CWE entries.
What does it mean CPE?
CPE is the acronym for “Common Platform Enumeration“. As NVD report, it consist on a “…structured naming scheme for information technology systems, software, and packages. Based upon the generic syntax for Uniform Resource Identifiers (URI), CPE includes a formal name format, a method for checking names against a system, and a description format for binding text and tests to a name”.
Understanding CPE syntax is necessary to use Pentest.IT features as well!
What is CVSS?
CVSS is the acronym for “Common Vulnerability Scoring System“. Its value can be in a range between 0 and 10. Grater value stay for greater risks. Actually CVEs are mapped to CVSSv2 Base Score. More information about CVSS are available in first.org website.
What is a patch?
In this scenario a patch is a piece of software applied to another one, designed to fix a vulnerability or a generic software flaw.
What are the available informations provided by Pentest.IT?
The service provides the followind items:
- Full list of published vulnerabilities with an associate RSS feed for the latest 25 items;
- Published vulnerabilities for any specific vendor with an associate RSS feed for the latest 25 items;
- Published vulnerabilities for a specific software with full CPE notation and an associate RSS feed for the latest 25 items;
- Published vulnerabilities for specifics product family (go to “The concept of Product Family“) with an associate RSS feed for the latest 25 items;
- Full list of “Common Weakness Enumeration”;
- Full list of “Common Attack Pattern Enumeraion and Classification”.
The concept of “Product Family”
Pentest.IT consider a “product family” as the aggregation of all vulnerabilities regarding a specific vendor and a specific product. In the CPE notation, two version of the same product have differents CPE entries (of course). But consider the case on you manage a set of machines where various version of the same software (aka CPE product) are installed (this happens often in the real world).
To aggregate these informations in a single view use this feature.
Permalinks structure for HTML resources
Pentest.IT has a basic set of API based on the permalinks structures.
- Single CVE entry: /cve-YYYY-CODE.html (example);
- Focus on specific vendor: /vendor-CPE_VENDOR.html (example);
- All CVE for a specific vendor: /vendorcve-CPE_VENDOR.html (example);
- Focus on a specific product family: /product/family/CPE_VENDOR:CPE_PRODUCT.html (example);
- All CVE for a specific product family: /product/family/all/CPE_VENDOR:CPE_PRODUCT.html (example);
- Focus on a specific CPE dictionary entry: /cvesoftware/CPE_PART:CPE_VENDOR:CPE_PRODUCT:CPE_VERSION:CPE_UPDATE:CPE_EDITION:CE_LANGUAGE.html (example).
Permalinks structure for RSS feed resources
Pentest.IT provides the following RSS feed:
- Latest 25 vulnerabilities: http://www.pentest.it/cve.rss;
- Specific vendor vulnerabilities: /vendor-CPE_VENDOR.rss (example);
- Product family vulnerabilities: /product/family/CPE_VENDOR:CPE_PRODUCT.rss (example);
- Specific CPE entry: /cvesoftware/CPE_PART:CPE_VENDOR:CPE_PRODUCT:CPE_VERSION:CPE_UPDATE:CPE_EDITION:CPE_LANGUAGE.rss (example).
Pentest.IT has the ability to map in a single view all available attributes:
- CVE Code
- Published date
- Updated date
- Description
- CVSS score and details
- Affected OS(s)/Application(s)/Hardware(s)
- Affected product family
- References
- CWE reference and related CAPEC
- MS Patches (only for Microsoft related CVEs)
- Related CVEs
- JSON data representation
RESTful API for CVE entries
Pentest.IT has the ability of give you all CVE informations in a single JSON stream. Use the following permalink structure:
- http://www.pentest.it/cve-AAAA-CODE.json (example).