Someone noticed the old Pentest.it is now “infosec.cert-pa.it”. Since last time I wrote about it, the service has been improved with new features and sections focused on IoC collection and correlation.
What’s new.
Two new modules added to the web application:
Blocklist Module
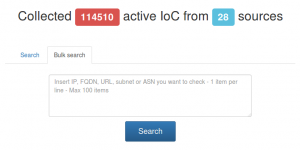
The blocklist module collects IoCs from a large number of public lists. The web application allow you to search for URLs, IPs and FQDNs. You can search a single item using the “Search” tab. The query result display you if an exact match will be found and also the similar results.
Using the “Bulk Search” tab you can submit 100 items per query, but in this case only the exact match will be displayed. In any case you can export the results in CSV format.
Analyzer Module
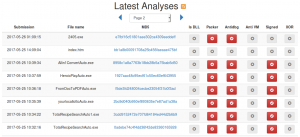
The analyzer module consists in a automatic souspicious file analyzer. Any page contains the static analysis of the file and a basic bahavior analysis. The submitted files are taken by OSINT sources (and not only). You can subscribe the RSS feed, if you want to be notified for every submitted file.
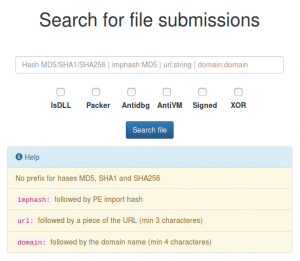
The easiest way to find information is the use of the dedicated search engine. You can search by MD5, SHA1 and SHA256 just submitting the correspondent hash.
Special searches are available with the use of the following keywords:
- imphash:$IMPORT_TABLE_HASH
- domain:$FQDN
- url:$URL_HOSTING_MALWARE
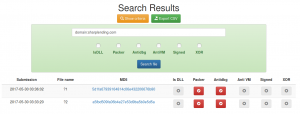
The search results page use a permalink structure you can use for further searches. The search results are exportable in CSV format. The CSV link is availables on the same page and reflects the permalink structure of the web search.
A new way to aggregate data is the use of the tagging system. Occasionally a report includes comments. Often comments are used to add a keywords, making the report aggregable via tag search. Just an example using one of the latest detected threat: #EternalRocks.
Any report can be exported in PDF format, at this time with limited information.
Hope this help.